IT/OT Convergence – The Essential Guide

With the increasing connectivity requirements and need for data analytics from industrial environments, the once clear distinction between the information technology (IT) and operational technology (OT) systems, processes, and people are getting blurred. The air gap, if it ever truly existed, is long gone. The increased connectivity and criticality of these systems create greater challenges for their adaptability, resilience, safety, and security. Industrial companies, even ones that do not adore the term IT/OT Convergence, need to understand the inherent risk across both these domains. Perhaps IT/OT Collaboration is a better term, but whatever label you use to designate this nexus point, it is well beyond time that we all recognize and appreciate the challenge it presents.
The air gap, if it ever truly existed, is long gone.

The Industrial Internet of Things (IIoT) and Industry 4.0
The growth of the industrial internet of things (IIoT) and Industry 4.0 technologies have strengthened the industrial enterprises’ need to monitor and control automated processes further driving IT/OT Convergence. Such improvements in technical processes increase the productivity of machines and eliminate manual operations or operations done by older machines while delivering innovative breakthroughs in cost and performance.
The primary aim of these new waves of innovation is to increase efficiency and productivity. The primary challenge is to do so, without compromising the intrinsic structure of these systems that are built to ensure safety, resiliency, and reliability.
IT/OT Convergence is essentially a confluence of distributed computing power, data processing, and the OT systems that manage and control industrial operations. The need to combine process automation and business intelligence is driven by business demands.
The key to successfully combining these two worlds is to keep your eye on the prize. The common goal must be securing the entire company and the path forward involves finding common ground, this is the only approach for successful IT/OT Convergence. This approach guarantees the enterprise continues to safely and efficiently remain competitive in an increasingly connected and insecure world. A lack of trust, understanding, and/or collaboration between OT and IT departments can have a devastating impact on the security posture of an organization.
The key to successfully combining these two worlds is to keep your eyes on the prize.
With the intensification around IT/OT Convergence, it is vital to start with the people on both sides of the fence, build trust around the common goal, and ensure that the goal is simple: To understand and measure the inherent cyber risk across the entire industrial enterprise. The risk must be understood in terms of the business risk, not technology. What the IT and OT folks need to do is understand each other, their distinct world views, build confidence as a team, and then together work out how to minimize cyber risk to the organization from end to end. Sounds simple, right?
The industrial control systems (ICS) omnipresent in the OT environment, are often highly interconnected and mutually dependent. Historically ICS/OT/SCADA were isolated systems running proprietary control protocols using specialized hardware and software and functioned solely in the OT environment. The OT environment evolved “A long time ago in a galaxy far, far away” from IT.
The OT environment evolved “A long time ago in a galaxy far, far away” from IT.
Policies and procedures employed by IT teams focus on the ‘CIA triad’ of Confidentiality, Integrity, and Availability. In contrast to OT’s specialized equipment, the IT toolset is primarily made up of off-the-shelf hardware and operating systems, and a standard set of applications better equipped to support business operations and tasks. The more ‘standard,’ the better for IT purposes. They are easily deployed, managed, upgraded, and secured (patched).
IT networks, hence, tend to be more dynamic and adaptable to rapid changes which is quite the opposite of the OT environment. The lifetime of IT equipment is considered as three to five years, while it is not uncommon to find OT/ICS equipment that is well over 20 years in service and yes, still up and running.
The increasing proliferation of IT capabilities into OT/physical systems can provoke behavioral changes in the structure of the enterprise with underlying security implications. The deployment of industry-standard computers, operating systems (OS), and network protocols have led to an entire world of IT within the OT environment. The once hidden realm of OT has opened itself to the outside. Who should secure this? How should it be done – standard IT cybersecurity policies and procedures can cause disaster within the OT environment.
Standard IT cybersecurity policies and procedures can cause disaster within the OT environment.
We have already observed the emergence of collaborative teams – IT security and operational teams that build a joint approach, platforms, processes, and technology to keep the enterprise secure while reducing risk. This joint team or taskforce works to share accountability for the priorities included in maintaining the productive state and security of the enterprise’s environment, as the organization matures its outlook towards cyber risk mitigation.
By bringing together security and operational professionals, and preventing security from being a siloed department, industrial organizations can improve their defenses against growing levels of cyber risks, as the threat landscape becomes increasingly more complex and worrying.
Using this proactive joint approach, IT/OT Convergence identifies the “crown jewels” regardless of which part of the organization they reside and creates streamlined multidisciplinary playbooks that deliver greater visibility into security vulnerabilities and the cyber kill chain, improve the process for threat hunting and remediation keeping systems agile and aligned.
IT/OT Convergence identifies the “crown jewels” regardless of which part of the organization they reside
IT and OT personnel come to the table with different agendas, which must be aligned for a smooth, reliable, and efficient team functioning. Lack of trust, understanding, and working relationship between OT and IT departments can have a devastating impact on the security posture and residual cyber risk of an industrial organization.
Though the two sides come with different operating procedures and roles to play. The respective teams have considerably differing worldviews and for very good reason. OT engineers and plant managers are all about keeping the production going, making sure it is safe, while figuring out how to increase productivity and output, and how to keep the machine going, no matter what.
The respective teams have considerably differing worldviews and for very good reason.
The IT cybersecurity view is all about protecting the company’s IP, information systems, customer data, and the like. It is not a matter of right or wrong, just an objective approach to identifying inherent cyber risk in terms of the business risk appetite. Everyone involved in the process must step outside their “world view,” and look at the issue in terms of a business strategy.
OT engineers are from Mars and IT SecOps professionals are from Venus

Different world views
Just like in the famous relationship book by John Gray, ‘Men Are from Mars, Women Are from Venus,’ the folks behind the IT and OT networks are extremely different with disparate perceptions, worldviews, and purpose.
As IT/OT Convergence becomes the ‘new normal,’ industrial enterprises need to find a way to work together and find answers through reasoning and mutual understanding. Both environments have differing practices, which can often translate into conflict and disparate approaches that create inefficiencies, weaken security postures and open the organization to greater security threats and risks.
Many organizations today have a CISO (chief information security officer), who works towards setting up a framework that manages cyber risk by establishing and overseeing relevant security and governance practices. The CISO steers the company’s cybersecurity vision, strategy, and program to make sure that information, assets, and technologies are adequately protected in line with the company’s risk appetite. The CISO and the IT/SecOps teams are often tasked with the overall accountability for cybersecurity, with the right tools, expertise, and methodologies necessary to secure the enterprise and they often control the budget.
However, IT SecOps personnel rarely have the necessary expertise or insights to understand the company’s operational and process control technology. This sharply differs from the OT systems, which are usually capital-intensive, massive legacy systems, which may not always be modern or state-of-the-art. Very often, the nature and composition of these systems do not allow them to be upgraded, as they are delivered by OEM (original equipment manufacturer) vendors. So, the only way, the OT equipment could get an update or a patch is if they get it from the vendor themselves.
IT SecOps personnel rarely have the necessary expertise or insights to understand the company’s operational and process control technology.
Let’s say, Siemens sold an HMI (Human Machine Interface) running on Windows 95, it is running their HMI software, it might be running an antivirus that also came through Siemens. The plant manager, or engineer, can’t actually touch it – they can’t patch it, they can’t upgrade it, they can’t do anything that may void the accountability of the OEM vendor. Very often, it is this knowledge-trust gap, including their mindset of quick-fix solutions, which leads IT SecOps personnel to assume that the same approach they use to secure their IT networks will work in the OT environment.
As IT/OT Convergence rises, IT teams need to work alongside their OT engineers to ensure they have a deep understanding and appreciation of both what needs to be protected, and how to protect these assets without disrupting production. For IT/OT collaboration to be successful, both sides must have something to gain and a way to contribute to the overall business bottom line.
What is the IT in IT/OT Convergence?
The Purdue Model, adopted from the Purdue Enterprise Reference Architecture (PERA) structure developed in the 1990s, refers to a commonly accepted concept-based model used in ICS network segmentation. The architectural framework was developed by Theodore J. Williams and members of the Industry-Purdue University Consortium for Computer Integrated Manufacturing and was meant to be resilient, while encoding it into standards, such as ANSI/ISA-95 and IEC 62264. It delivers foundational language for control systems security regulatory controls, such as IEC 62443 and NIST SP800-82 benchmarks.
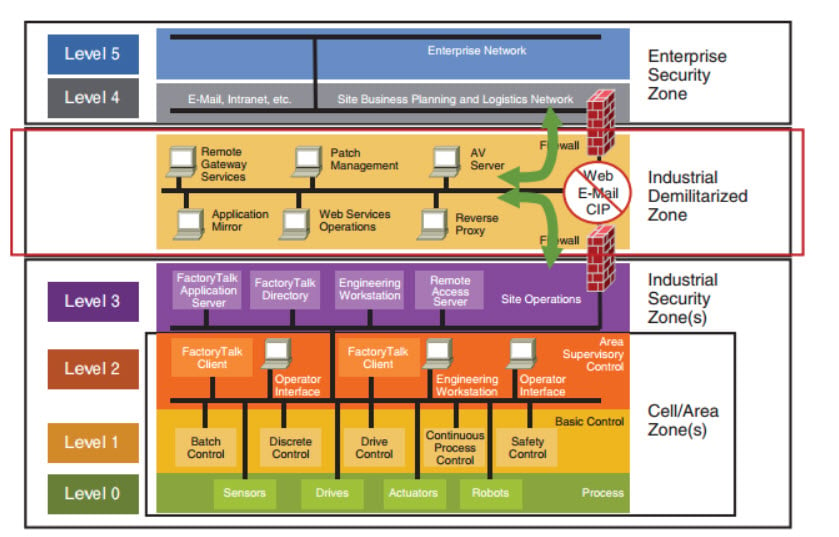
The classic Purdue reference model
The Purdue Model segments devices and equipment into hierarchical functions that show the interconnections and interdependencies of the main components of a typical ICS. The Perdue Model delineates security boundaries between users, ICS networks, and business networks, and shows how these boundaries have blurred in recent years as IT/OT Convergence gained importance.
Current Purdue architecture breaks down OT and IT into six functional levels that run from Level 0 to Level 5 across three zones.
- Level 0 (physical process) is where the physical equipment that defines the actual physical processes is found.
- Level 1 (basic control) hosts the control devices such as sensors, pumps, and actuators, which sense and manipulate the physical processes in order to drive efficiencies.
- Level 2 (control systems) houses the ICS including HMI and SCADA systems in order to supervise, monitor, and control physical processes.
- Level 3 (manufacturing execution systems) is where the production workflow is managed on the manufacturing floor using customized systems for various functions, including batch management, record data, and manage operations and plant performance. These systems also put together lower-level data that gets pushed up to the higher-level business systems.
- Level 3.5 – Between Level 3 and Level 4 of the Purdue Model lies the Demilitarized zone (DMZ) which has been created very much as an outcome of IT/OT Convergence. This level consists of the security systems such as firewalls and proxies, which moderate/police bidirectional data flows between OT and IT systems. The DMZ permits data exchanged between the highly risky and connected business networks and low-connection, low-risk ICS networks.
- Level 4 (IT systems) consists of IT networks such as enterprise resource planning (ERP) systems, database servers, application servers, and file servers that enable the enterprise to drive business logistics systems.
- Level 5 (corporate network) covers the enterprise IT systems that cover connections with the public internet.
Many “IT-related” OT security vulnerabilities reside deep within the ICS network, meaning they apply to equipment on Levels 0 to 3 of the Purdue Model, which includes engineering workstations, PLCs, sensors, and industrial controllers. These vulnerabilities exist due to the deployment of legacy systems, which may often be outdated, out of service systems, end-of-life, and/or not adequately security patched, apart from not receiving regular security updates. While some claim that the model may have outlived its usefulness, it is still commonly referred to, even if it not as sanctified as it once was.
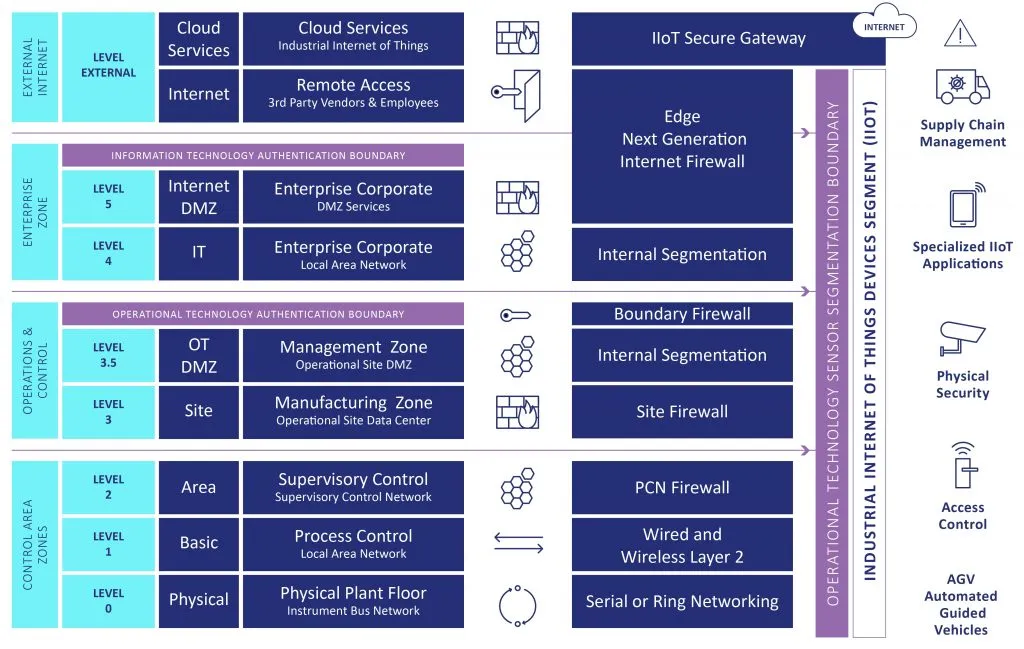
An updated take on the Purdue Model to include IIoT and Cloud – Operational Technology Cyber Security Alliance (OTCSA)
Frequently Asked Questions on IT/OT Convergence
What is the OT in IT/OT Convergence?
As the backbone of industrial automation, the OT/ICS systems control a nation’s power electricity grid, water and wastewater, pharmaceuticals, oil and natural gas, transportation, chemical, pulp and paper, discrete manufacturing, and so on. Due to the nature of the work performed, these control systems cannot afford any sort of abrasions or abnormalities in the process systems themselves or in the equipment that may cause problems in reliability, productivity, or safety. The system cannot simply be taken down for an upgrade!
These systems focus on operational requirements while meeting the needs of physical safety of processes, people, and technology. These systems are designed to run consistently and continuously, often in oppressive and challenging environmental operating conditions. System and asset integrity are paramount, and failures or downtime can be costly and potentially catastrophic.
ICS includes SCADA (supervisory control and data acquisition) systems that enable industrial enterprises to control industrial processes locally or remotely, while monitoring, gathering, and processing real-time data. The control systems connect with devices such as sensors, valves, pumps, and motors, via HMI workstations, and records events into the database (data historian) to document performance and quality.
When legacy OT networks were originally designed and deployed, security wasn’t even on the drawing board. Very few thought there would be an external danger, based on the assumption that malicious actors lacked the knowledge to carry out attacks or that the isolated ICS systems used proprietary control protocols for their hardware and software, the environments were closed and thoroughly air-gapped. Often referred to by the term – Security by Obscurity.
Threats to control systems can come from a variety of actors, from state-sponsored terror groups to environmental hacktivists, not to mention natural disasters, as well as malicious or accidental actions by insiders. Attacks can cause severe damage, disable or shut down equipment, create environmental impacts, and/or endanger human life.
Industrial enterprises are constantly evolving – while SCADA systems control and maintain efficiency, companies are adopting new IT solutions to create new business opportunities, data is being distributed for smarter decisions and preventive maintenance helps reduce downtime. While IT/OT Convergence supports IT capabilities, it provides significantly less isolation to the OT environment and critical production from the outside world than legacy environments, exposing these systems to greater cyber risk.
What’s driving IT/OT Convergence?
IT/OT Convergence creates a synergy that provides business operators with strategic insights that can significantly improve internal processes, business decisions, productivity and competitiveness. By integrating the two environments, organizations can bridge gaps and upgrade operational performance by working around a unified set of objectives and KPIs (key performance indicators) that constantly measure how effectively a company is achieving organizational objectives. In short, they can build sustainable competitive advantages to outmaneuver their industry counterparts.
An integrated, connected framework provides organizations with predictive and preventive maintenance data. This data enables the business to implement maintenance plans that optimize productivity, while closely monitoring equipment to increase reliability and availability. IT/OT Convergence will reduce breakdown time and related costs, while maintaining optimal working conditions and operational uptime which is crucial in industrial sectors. Analytics will enhance the life expectancy of assets, by decreasing high turnover rates that can be costly to a business’s bottom-line.
As edge compute moves into the industrial environment and clouds are connected to process data in real-time, organizations can convert machine-generated data into actionable insights quickly, to ultimately help with managerial decision-making. The ability to remotely and in real-time, keep tabs through asset tracking, monitoring, and troubleshooting also prepares the organization to better respond and act.
The upside to this technology is often just too crucial to be ignored and will undoubtedly lead to greater adoption within industrial companies, particularly in verticals like manufacturing.
IIoT and IT/OT Convergence
Increased adoption of IIoT and Industry 4.0 technologies particularly in the sectors such as manufacturing and BMS is driving the need for industrial hardware like gateways, PLCs, and remote I/O modules to integrate with edge compute, devices, IT-enabled software, and applications that deliver productivity, reliability, and safety in an increasingly connected organizational structure.
The IIoT architecture is comprised of a massive network of network-connected devices and sensors, designed to collect and transmit data upstream. Using this data, enterprises can enhance business processes, bring increased automation providing real-time optimization, scalability, productivity, and operational efficiency. The proliferation of IIoT devices and platforms across the industrial infrastructure has led to complex integrations with network sensors and managed by software, providing advanced analytics.
Wireless networking devices, for example, enable business intelligence data to be extracted from the industrial equipment and then filtered, prioritized, and subsequently processed. They can also expose the environment to new attack vectors and they can significantly increase the potential attack surface.
IIoT platforms often send data directly to the cloud. Edge devices make sure that the right data gets sent to the right system, at the right time, with the right priority. Rather than existing in silos, the data generated by machines and processes can be converted into valuable insights and transmitted across IT networks to various departments within the organization. This data can provide significant benefits, but it most definitely alters the company’s security posture and challenges.
Why IT/OT Convergence will continue to gain momentum
IT/OT Convergence goes well beyond technological issues. It provides organizations with accurate information that is delivered to people, machines, switches, sensors, and devices at the right time and in the best format to help with decision-making. Using a high-level overview of the process is required to implement, operate, monitor, review, maintain and improve the information security program.
The two realms of IT and OT that traditionally evolved independently, often completely oblivious to the other’s existence are now forced to come together and work out a supportive environment that necessitates changes in workplace philosophies and rethinking corporate culture.
Many of the challenges in IT/OT Convergence are people/process problems rather than technical. Threats are increasingly complex and unpredictable, and the malicious actors do not necessarily have to specifically target industrial enterprises to have a devastating impact. Indeed, there are already many examples of ransomware, not designed to target industrial enterprise having a considerable impact on production.
The industrial cybersecurity strategy must be about the collaboration between the IT and cyber-physical security to comprehend the inherent risks of cyberattacks, and the cyber-physical security measures that should be put in place to mitigate them and reduce the risk to acceptable levels.
As boards and company management ask tough questions on cybersecurity and cyber risk within the organizational structure, people from the IT and OT realms must build trust amongst themselves, understand the other’s mindset, and then work towards the common goal of securing industrial enterprise and minimizing cyber risk. Unless they mend the bridges, the organization will fail to meet risk appetite and leave the company exposed.
What is IT/OT risk Convergence?
With the spread of IT functions into OT environments, and the subsequently enhanced interconnectivity, some of the cybersecurity risks associated with IT systems have crept into OT networks as they become more accessible. In many industrial companies, there is now systemic interdependent cyber risk between the OT and IT sides of the house.
As the IT and OT networks further integrate, creating strong boundaries between business and process control networks can reduce the number of vulnerabilities and attack pathways that a potential hacker may exploit to gain unauthorized access into these critical systems, thereby reducing IT/OT risk convergence.
What are the common challenges in OT security?
Common challenges faced in the OT security environment are:
- Lack of visibility due to an incomplete picture of endpoints
- Presence of legacy systems in regular need of security patches and software updates, which were often unavailable
- Little to no control over security policies
- Lack of dedicated trained OT cybersecurity staff on-site
- Lack of employee awareness/training with regard to social engineering
- The absence of necessary information prevent organizations from getting the latest security tactics and protocols
- Heightened regulatory/compliance pressure faced by (some) ICS and SCADA environments
Why are IT and OT so different?
IT systems consist of:
- Hardware: made up of computers, network equipment, and physical servers
- Software: consisting of applications, operating systems, and virtualization capabilities.
- Data networks
The IT environment is configured to cope with advancing business requirements, applications, and user needs that tend to be more business-oriented.
OT systems consist of:
- Control systems
- Data acquisition systems
- Industrial networks
The OT environment utilizes compute networking, and storage technologies to process or communicate information related to the management of physical processes.









